- Laptop Model
- Optiplex 7090
Hey everyone, I'm new to the forums and just needed some help on an Optiplex 7090 8FC8.
I've tried various patchers and keep getting:
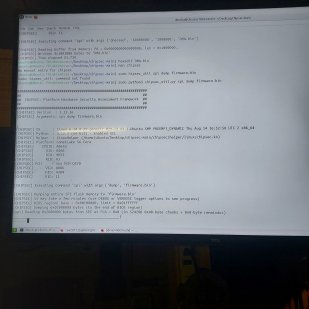
Searching for Intel signature...
Intel signature found at offset 0x10
Checking for first pattern...
Almost done! Checking second pattern...
Patching failed: No patterns found
I keep getting no patterns found, but I dumped my rom with chipsec_util spi dump and chipsec_util spi read after signing the helper kernel driver to get chipsec fully running.
8FC8 seems highly locked down, but there has to be a process for in system programming, I believe. I can flash the BIOS region and I have a TON of info and data on the system, flash, regions and even extracted parts of the firmware.
Here is the method I used to do all this on the system that is locked:
Install Ubuntu on an unlocked system that has secure boot enabled and put it in the locked system once installed and bootable.
Boot Ubuntu, update, upgrade, install various tools and utilities as well as build-essentials.
Install and setup chipsec, creating the kernel helper module.
Create a key for signing and register it, reboot, enroll MOK and boot back to Ubuntu.
Sign the kernel module and install it.
Run chipsec and see how secure 8FC8 actually is for yourself.
Attack S3 Boot Scripts to gain SMI/SMM write permission and SPI write access?
What are the patterns the patchers are looking for?
I'm able to write to BIOS region, but need to know where to clear the password. I don't have access to write to ME or other regions through internal in-system programming, though.
Thanks!
Here is some of what I've collected so far:
I've tried various patchers and keep getting:
Searching for Intel signature...
Intel signature found at offset 0x10
Checking for first pattern...
Almost done! Checking second pattern...
Patching failed: No patterns found
I keep getting no patterns found, but I dumped my rom with chipsec_util spi dump and chipsec_util spi read after signing the helper kernel driver to get chipsec fully running.
8FC8 seems highly locked down, but there has to be a process for in system programming, I believe. I can flash the BIOS region and I have a TON of info and data on the system, flash, regions and even extracted parts of the firmware.
Here is the method I used to do all this on the system that is locked:
Install Ubuntu on an unlocked system that has secure boot enabled and put it in the locked system once installed and bootable.
Boot Ubuntu, update, upgrade, install various tools and utilities as well as build-essentials.
Install and setup chipsec, creating the kernel helper module.
Create a key for signing and register it, reboot, enroll MOK and boot back to Ubuntu.
Sign the kernel module and install it.
Run chipsec and see how secure 8FC8 actually is for yourself.
Attack S3 Boot Scripts to gain SMI/SMM write permission and SPI write access?
What are the patterns the patchers are looking for?
I'm able to write to BIOS region, but need to know where to clear the password. I don't have access to write to ME or other regions through internal in-system programming, though.
Thanks!
Here is some of what I've collected so far:
Attachments
-
12.5 MB Views: 1